|
Syllabus: Prelims GS Paper I : Current events of national and international importance.
Mains GS Paper III : Challenges to internal security through communication networks, role of media and social networking sites in internal security challenges, basics of cyber security
|
Context
As the world settles into the work-from-home mode, there’s been a new challenge to contend with cyber security. Last incident of hacking Twitter Accounts in the recent Bitcoin scam has made it a matter of immediate concern.
Background
The country’s nodal cyber security agency Indian Computer Emergency Response Team (CERT-In) has issued a notice to Twitter requesting information on a recent hacking of high-profile accounts, including the number of affected Indians and the overall impact. The agency has also asked how Twitter is working to solve the vulnerabilities.
Recently, hackers conducted unprecedented takeovers of some of the platform’s highest-profile accounts, such as US presidential candidate Joe Biden, former US President Barack Obama, and billionaire Elon Musk.
Cyber Security
Cyber security refers to the body of technologies, processes, and practices designed to protect networks, devices, programs, and data from attack, damage, or unauthorized access. Cyber security may also be referred to as information technology security.
|
Challenges of Cyber Security
- Network security
- Application security
- Endpoint security
- Data security
- Identity management
- Database and infrastructure security
- Cloud security
- Mobile security
- Disaster recovery/business continuity planning
|
Importance of Cyber Security
Cyber security is important because government, military, corporate, financial, and medical organizations collect, process, and store unprecedented amounts of data on computers and other devices. A significant portion of that data can be sensitive information, whether that be intellectual property, financial data, personal information, or other types of data for which unauthorized access or exposure could have negative consequences.
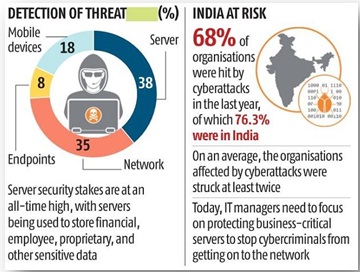
Last month, the Government of India, too, had issued a warning of a large-scale cyber attack in the country. Attackers, the advisory said, may use Covid-19 as a ploy to steal personal and financial information of citizens.
Steps taken by the Government to Manage Cyber Security
- Establishment of National Critical Information Infrastructure Protectio Cyber Security Challengesn Centre (NCIIPC) for protection of critical information infrastructure in the country.
- All organizations providing digital services have been mandated to report cyber security incidents to CERT-In expeditiously.
- Cyber Swachchhata Kendra (Botnet Cleaning and Malware Analysis Centre) has been launched for providing detection of malicious programmes and free tools to remove such programmes.
- Issue of alerts and advisories regarding cyber threats and counter-measures by CERT-In.
- Issue of guidelines for Chief Information Security Officers (CISOs) regarding their key roles and responsibilities for securing applications / infrastructure and compliance.
- Provision for audit of the government websites and applications prior to their hosting, and thereafter at regular intervals.
- Empanelment of security auditing organisations to support and audit implementation of Information Security Best Practices.
- Formulation of Crisis Management Plan for countering cyber attacks and cyber terrorism.
- Conducting cyber security mock drills and exercises regularly to enable assessment of cyber security posture and preparedness of organizations in Government and critical sectors.
- Conducting regular training programmes for network / system administrators and Chief Information Security Officers (CISOs) of Government and critical sector organisations regarding securing the IT infrastructure and mitigating cyber attacks.
Way Forward:
The most difficult challenge in cyber security is the ever-evolving nature of security risks themselves. Traditionally, organizations and the government have focused most of their cyber security resources on perimeter security to protect only their most crucial system components and defend against known treats. Today, this approach is insufficient, as the threats advance and change more quickly than organizations can keep up with. As a result, advisory organizations promote more proactive and adaptive approaches to cyber security. Similarly, the CERT In issued guidelines in its risk assessment framework that recommend a shift toward continuous monitoring and real-time assessments, a data-focused approach to security as opposed to the traditional perimeter-based model.
Connecting the Dots:
Question for Prelims
Consider the following statements
1. CERT-In is a national nodal agency for responding to Computer security incidents.
2. CERT-In functions under the Ministry of Finance.
Which of the statements given above is/ are correct ?
(a) 1 only
(b) 2 only
(c) Both 1 and 2
(d) Neither 1 nor 2
Question for Mains
How does cyber hacking pose a security threat to India ? Discuss the strategies adopted by India to curb this menace.

 Contact Us
Contact Us  New Batch : 9555124124/ 7428085757
New Batch : 9555124124/ 7428085757  Tech Support : 9555124124/ 7428085757
Tech Support : 9555124124/ 7428085757